Portfolio Companies
Strategic technology leadership across diverse sectors driving innovation and growth

Melearn
EdTech
Bullmoon
NFT/Web3
Bullmoon Jr
EdTech NFT
Stock2morrow
FinTech
2Read
Digital Publishing
2morrow Group
Holding
TUBC
BlockchainTechnology Stack
Modern tools and frameworks powering enterprise solutions
Portfolio Gallery
Moments from conferences, partnerships, and innovation showcases across Southeast Asia

Natthawat Sawatdee speaking at Bitkub Blockathon 2024 about AI API pricing and blockchain innovation.

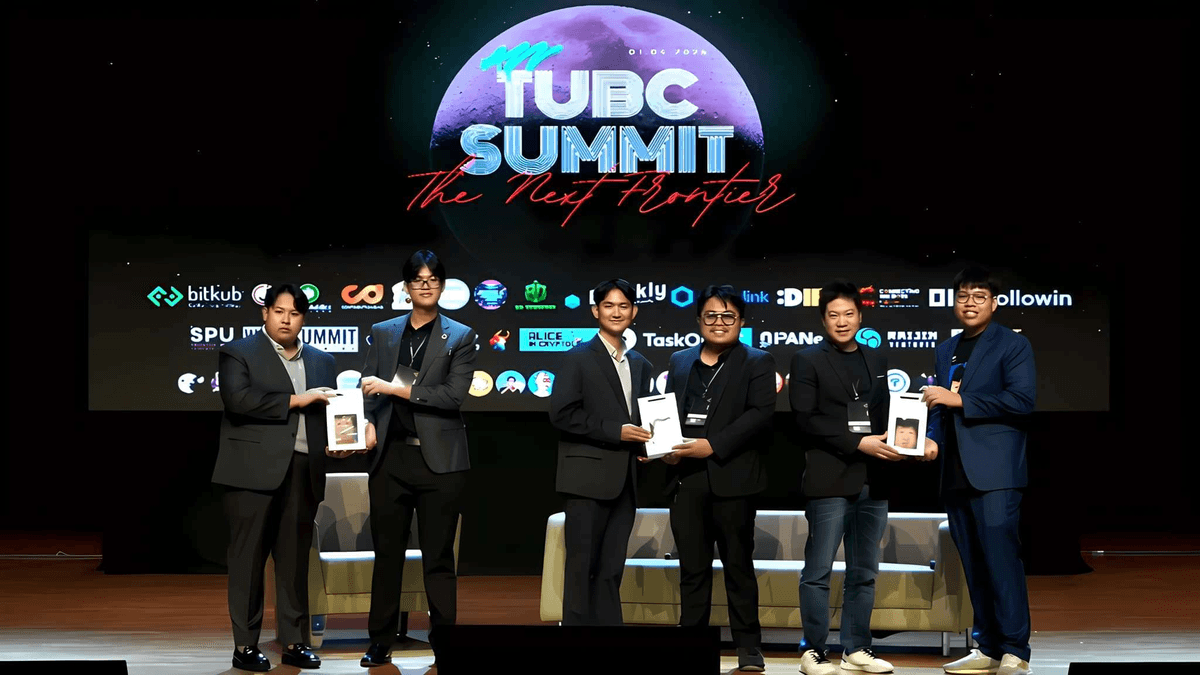
Natthawat presenting at Thammasat University Blockchain Summit (TUBC Summit).
Logo of Thai Blockchain Community, representing the blockchain ecosystem in Thailand.

Worldcoin project showcase, global digital identity and blockchain initiative.
TUBC Call event poster highlighting competition details and university engagement.
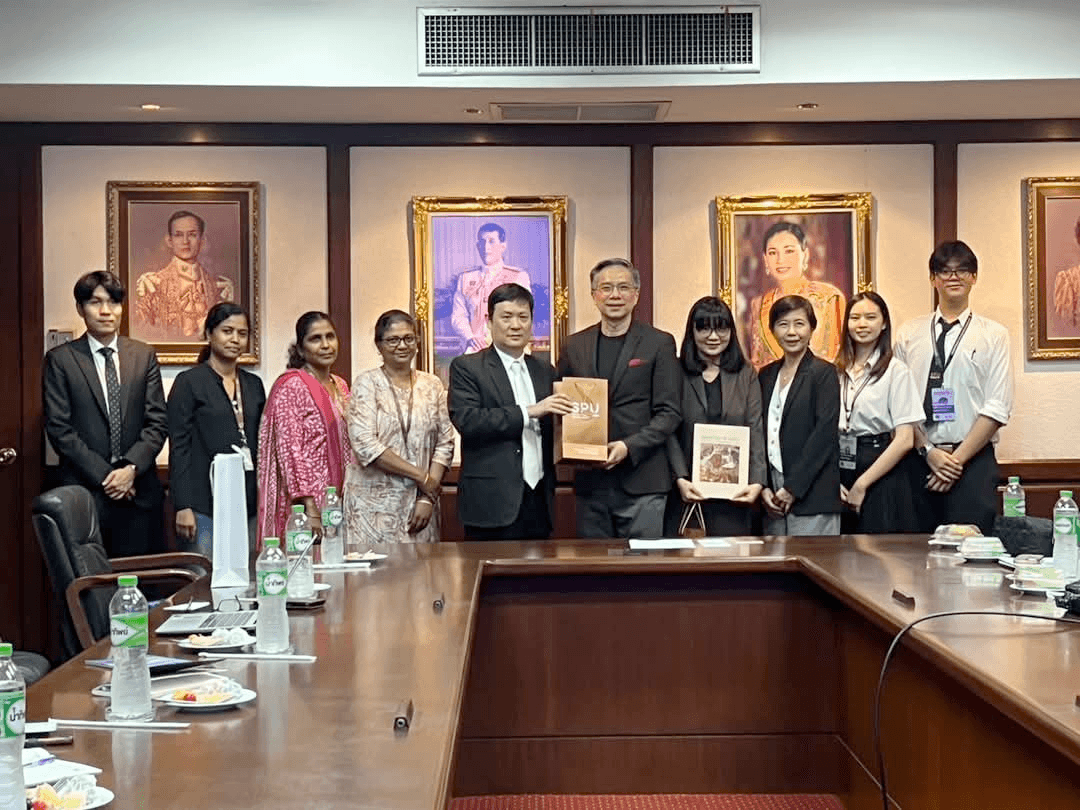
Natthawat welcoming the Ambassador and Consul from Chennai, India, together with professors from VIT University.

Natthawat with the Sripatum University team at a startup and innovation showcase.

Bitkub Blockathon 2024 event banner.
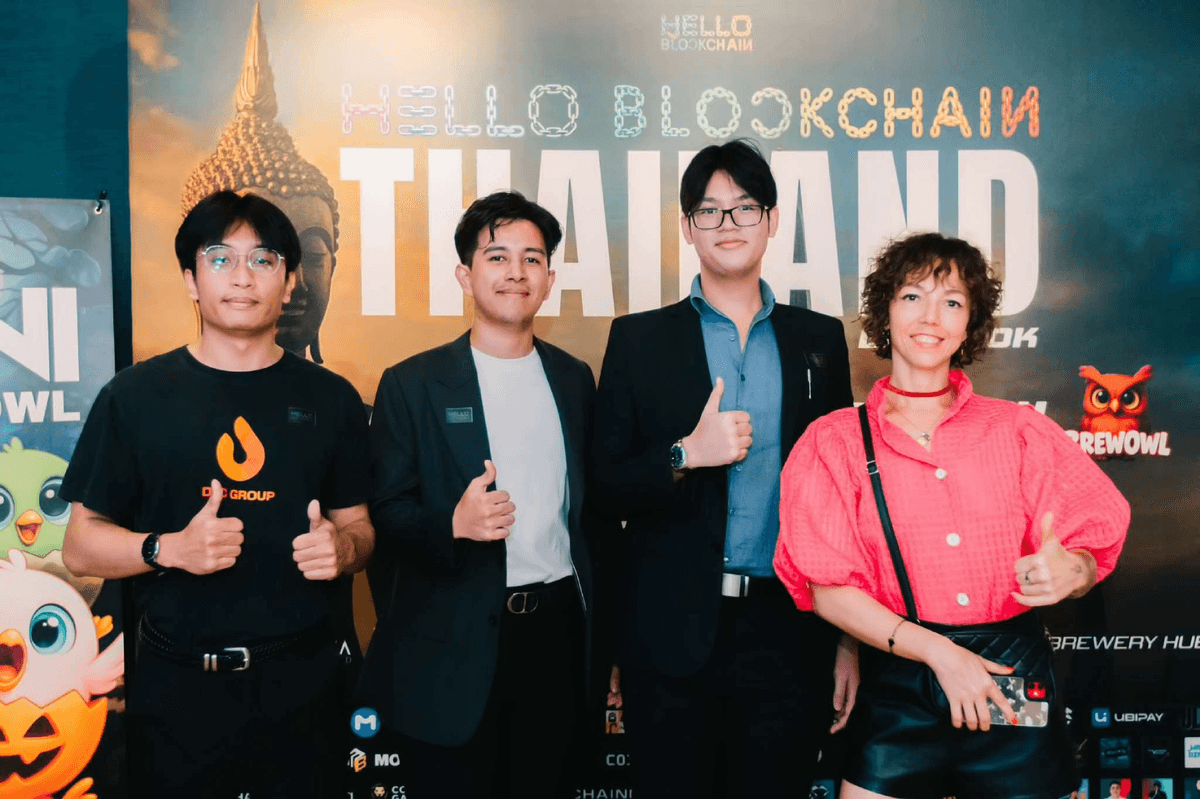
DTC Group at Hello Blockchain Thailand and Web3 community event.
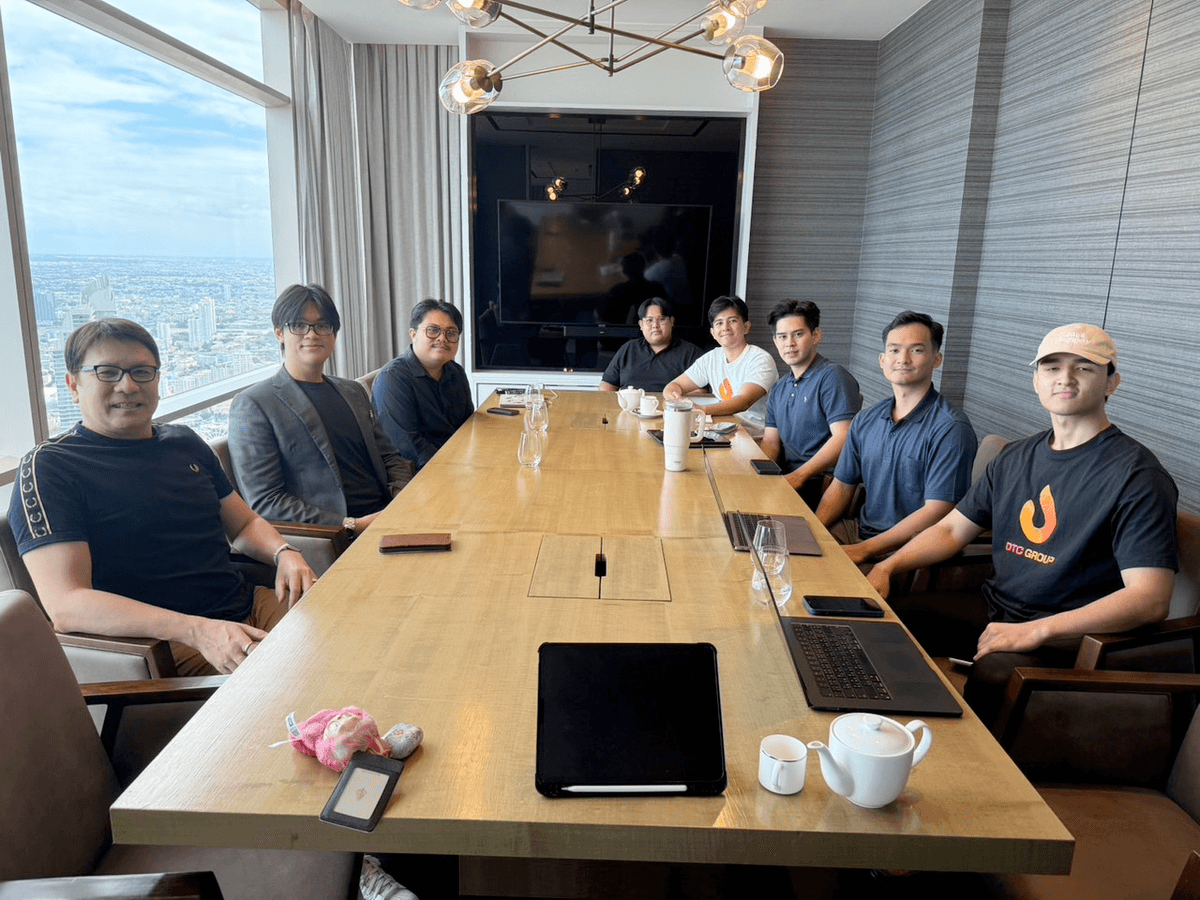
DTC Group in a joint meeting with Stock2morrow and Bullmoon Jr.

Natthawat Sawatdee participating at Bitkub Blockathon workshop.

Natthawat representing Sripatum University at an international AI training program hosted by VIT University, India (SPU x VIT collaboration).
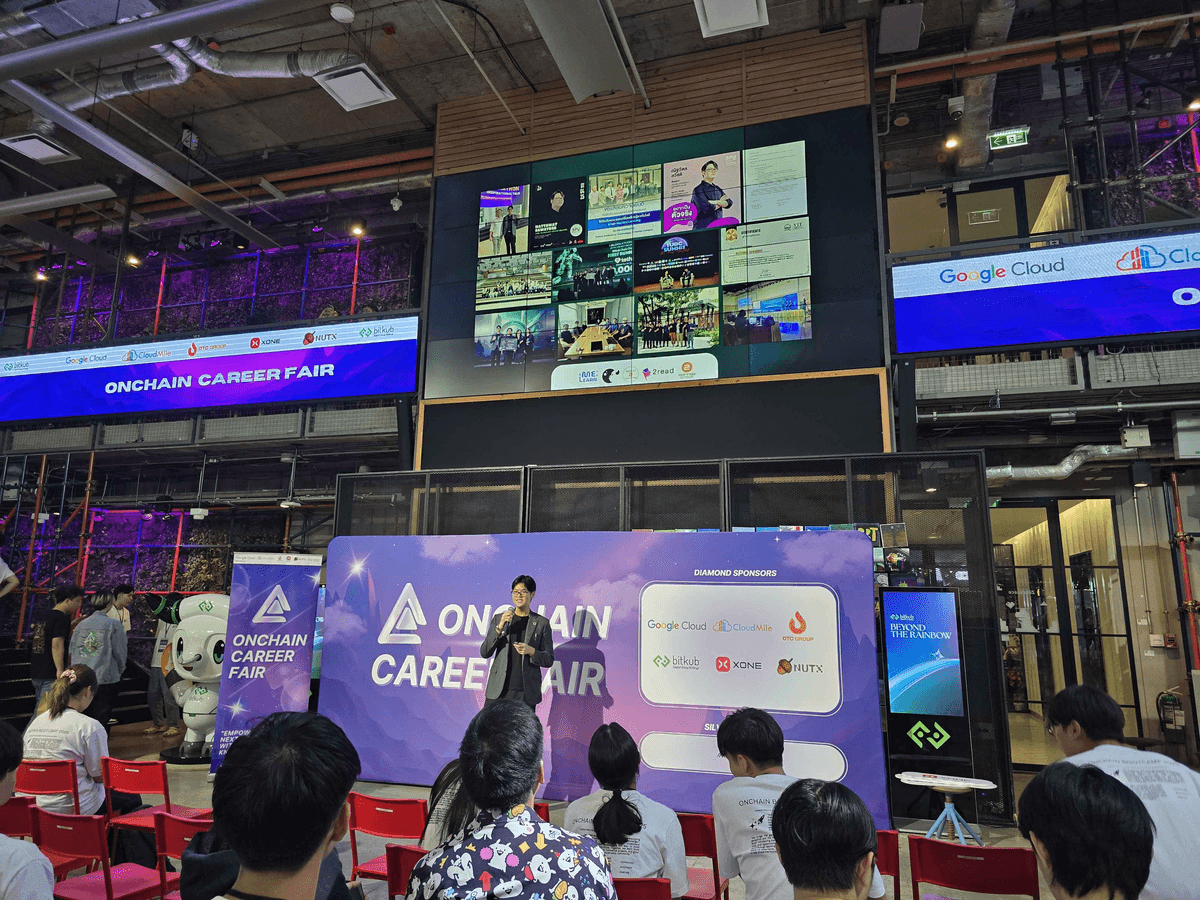
Natthawat, CTO of Bullmoon Jr, presenting to CU Blockchain Club about Bullmoon Jr with students from Thammasat University and Chulalongkorn University.

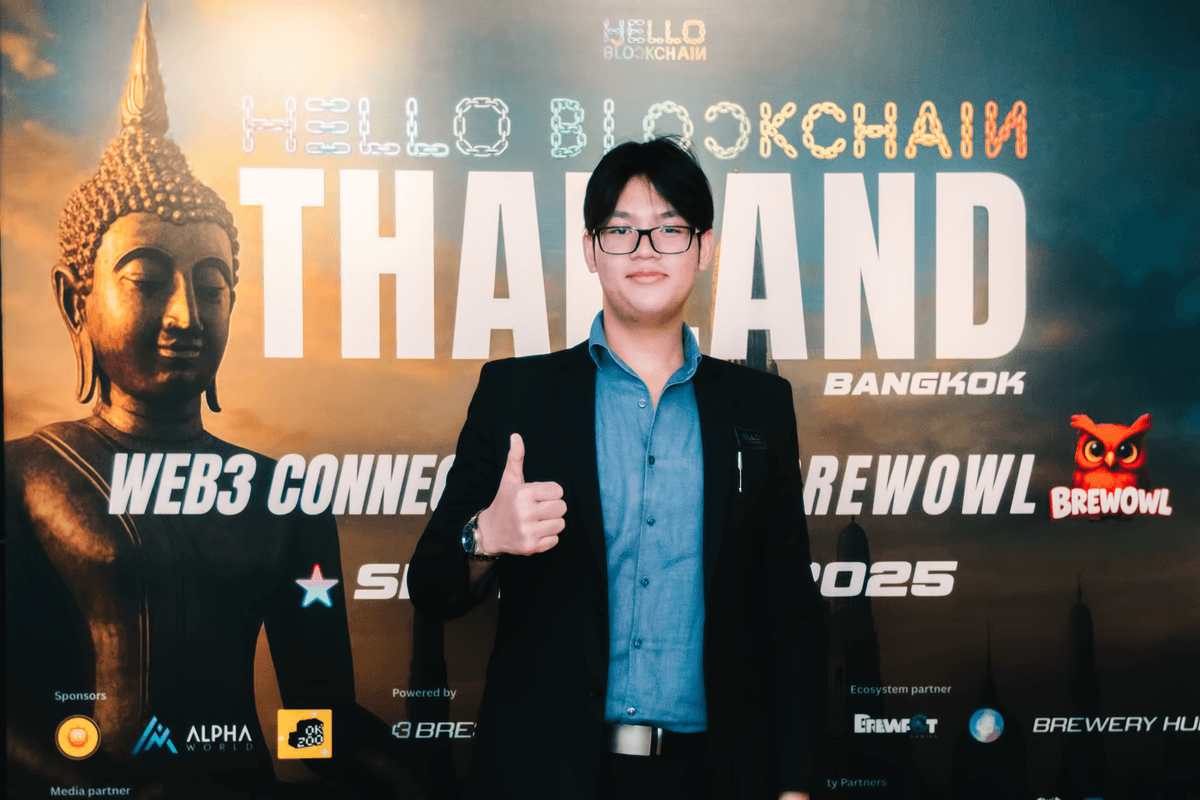
Personal poster of Natthawat Sawatdee showcasing technology leadership and achievements.

Natthawat moderating the TUBC x JIB AI event, featuring Thuntee Sukchotrat, CEO of JIB AI, as keynote speaker.
Professional Journey
Experience & Achievements
A timeline of projects, awards, and milestones that shaped my career in technology and innovation.
Independent Crisis Technical Consultant
ที่ปรึกษาอิสระด้านวิศวกรรมระบบ
กู้ระบบ Website / Application และ Payment Gateway ที่ล่มโดยไม่มีเอกสารอ้างอิง
Learn moreตัวแทนมหาวิทยาลัยศรีปทุมและประเทศไทย
VIT Chennai, India
ผู้แทนแลกเปลี่ยนด้าน AI & Machine Learning
เข้าร่วมโครงการแลกเปลี่ยนด้านเทคโนโลยีและนวัตกรรมระดับนานาชาติ
Learn moreHead of Technology & Engineering
2Read
ดูแลสถาปัตยกรรมระบบและการปรับปรุงเทคโนโลยีแพลตฟอร์ม 2Read
Learn moreActing Vice President of Technology
Stock2morrow Group
ลดต้นทุน Cloud Infrastructure ลง 25% ผ่านการเข้าร่วม Huawei Cloud HCPN
Learn moreActing Managing Director
2Read
ริเริ่มโครงการ 2Read+ และปรับโครงสร้างระบบเทคโนโลยีภายในองค์กร
Learn moreAI Book Search System for Thammasat University
Thammasat University
พัฒนาและออกแบบระบบค้นหาหนังสือด้วย AI
TUBC Summit 2025 Website & SEO Development
Thammasat University Blockchain Center
ออกแบบเว็บไซต์และ SEO ติดอันดับผลค้นหา 'TUBC summit' บน Google
Learn moreELT Data Processing System — 2Read
2Read
พัฒนาระบบ Extract–Load–Transform สำหรับการวิเคราะห์ข้อมูลภายในองค์กร
Learn morePersonal Website — natthawat.digital
Personal Project
พัฒนาเว็บไซต์ส่วนตัวและ SEO จนติดอันดับคำค้นหา 'natthawat sawatdee' บน Google
Learn moreเหรียญทอง นวัตกรรมสิ่งประดิษฐ์ระดับชาติ Smart Innovation
สำนักงานคณะกรรมการการอาชีวศึกษา
CEO โครงการ 'โดรนวัดฝุ่นแสดงผลค่าฝุ่นผ่านเว็บไซต์'
ได้รับเหรียญทองระดับชาติด้าน IoT และระบบตรวจวัดอากาศ
Learn moreที่ปรึกษาด้านเทคโนโลยี (Technology Advisor)
IMASS Research Project 2024
ที่ปรึกษาโครงงานวิจัย IMASS 2024
Application of Artificial Intelligence Technology in Financial Statement Analysis for Investment Decision Making: Case Study for the Stock Exchange of Thailand
ให้คำปรึกษาด้าน AI และ Data Analytics ในการวิเคราะห์งบการเงินเพื่อการลงทุน
Learn moreรองชนะเลิศอันดับ 1 Bitkub Blockathon 2024
Bitkub Labs Co., Ltd.
CTO ทีม Melearn
พัฒนาโปรเจกต์ Blockchain Application จนได้รับรางวัลรองชนะเลิศอันดับ 1 ระดับประเทศ
Bitkub NextGen Business Pitch 2024
Bitkub Academy
CTO / Startup Founder
เข้ารอบ 10 ทีมสุดท้าย โครงการนำเสนอธุรกิจเทคโนโลยีของเยาวชน
Learn moreFull Stack Web Developer & Web Architect
MONSTOPIA CO., LTD.
ที่ปรึกษาและผู้ดูแลระบบระยะยาว (LTS Consultant)
ออกแบบสถาปัตยกรรมเว็บและให้คำปรึกษาเชิงเทคนิคครบวงจร
Learn moreได้รับทุนตัวจริง (Talent Scholarship)
มหาวิทยาลัยศรีปทุม (SPU)
นักศึกษาทุนสาขาวิทยาการคอมพิวเตอร์และนวัตกรรมซอฟต์แวร์
ได้รับทุนระดับมหาวิทยาลัยจากผลงานด้านนวัตกรรมและเทคโนโลยี
Learn moreเหรียญทองแดง การแข่งขันทักษะวิชาชีพ สถานศึกษาอาชีวศึกษาเอกชน ระดับชาติ
สมาคมวิทยาลัยเทคโนโลยีเอกชนแห่งประเทศไทย (P-VEC)
ผู้เข้าแข่งขัน
ชนะเลิศเหรียญทองแดงในสาขาทักษะการสร้างเว็บไซต์
Learn moreAFTERKLASS Business KAMP Hackathon
AFTERKLASS x ธนาคารกสิกรไทย
CTO / ทีมผู้เข้าแข่งขัน 10 ทีมสุดท้าย
ผ่านเข้ารอบ 10 ทีมสุดท้ายด้านการพัฒนา Business Solution
Learn moreSwift Coding for iPad Training
Apple Education Program
ผู้เข้าร่วมอบรม
อบรม Swift Playground สำหรับการพัฒนาแอปพลิเคชันบน iPad
Learn moreThe Day Everything Broke
The Day Everything Broke
A true story of a startup’s worst nightmare: No IT, no docs, no clue—and then the entire business went offline.
Blind Organization: The Meltdown Begins
Q1, Year XXXX
No IT. No Docs. No Idea.
New year, total disaster. On January 1st, a promising Thai startup woke up to find its entire digital presence—website and app—dead. Not a single user could log in. The real punchline? There wasn’t a single IT person left in the company. Six months before, their IT manager quit. The core system had been built by an outsource team a year prior, with zero documentation, no ToR, no high-level diagrams, nothing. The downsizing wiped out any tech knowledge, any credentials, and any hope of a smooth recovery. When the outage hit, the management didn’t even know what language their backend used, what cloud provider hosted them, or where the code was. The startup was officially blind, lost in their own tech stack. Calls went out to software houses and every freelance dev they knew. Nobody wanted to touch it. Too risky, too messy, no information. Days passed. Customers left. Business froze. Hope faded. Nine days later, I—an independent software engineer—walked in, handed only a company laptop and the phone number of the CEO. No passwords, no system map, not even a clue. All I had was browser DevTools, Burp Suite, and a vague sense of curiosity. Time to start the digital autopsy...
Investigation Steps
- IT manager quit 6 months before the crisis.
- System built by outsource. No ToR. No docs. No architecture diagrams.
- No one in the company knew what tech or cloud was in use.
- January 1: Both website and app went offline. Zero access.
- All rescue attempts failed. No team dared to help.
- Nine days of total business freeze before anyone could even start troubleshooting.
The Digital Autopsy Begins
Day 9 - Entry Point
Hunting for a Pulse in a Dead System
With no credentials, no handover, and no map, the only way forward was digital forensics. I started by firing up F12 DevTools and Burp Suite, tracking network requests from the frontend just to figure out where the system was deployed. Piece by piece, scraping whatever IPs, endpoints, or cloud hints I could find, I began to reconstruct what the company no longer remembered about itself. The game was simple: guess, probe, document—repeat. Failure wasn’t an option. The clock was ticking, and the startup’s survival depended on brute-force curiosity and pure stubbornness.
Investigation Steps
- Started from scratch—no passwords, no accounts, no system diagram.
- Used browser DevTools to scan for active endpoints.
- Used Burp Suite to intercept and map network calls.
- Tracked down cloud footprints and guessed infra layout from IPs.
- Reverse engineered what the company once built, but completely forgot.
Container Abyss: Only Errors Inside
Day 10
Nothing But Errors
The only access I could get was through a half-broken VM running Docker. Once inside, there were logs—just not the kind you want: endless syntax errors. Nothing pointed to what broke. Was it their code, a 3rd party, or something deeper?
Investigation Steps
- Gained access to a VM running Docker and Nginx.
- Checked logs—found only repeated syntax errors.
- No traces of system-related errors.
- Couldn't tell if requests from Nginx were reaching the app.
- Still no documentation or reliable error trails.
- Needed to find a deeper root cause.
Reverse Engineering the Unknown
Day 11
Manual Code Review & Guesswork
With no source code repo or build process in sight, the only way forward was to decompile, grep, and trace by hand. Searched for API endpoints, error handlers, anything resembling a contract or standard. Everything was legacy code and hard-coded URLs.
Investigation Steps
- Manual code review via container shell access.
- Hunted for KBank API endpoints inside the codebase.
- Tried to identify where requests failed or were blocked.
- Mapped out what little architecture info could be found.
- Still no central documentation. It was all guesswork.
Network Trace & IP Whitelist
Day 12
Chasing the Network
Finally traced network paths out to KBank. Used my own dev machine to hit the endpoints, but got blocked—wrong IP. Tried from the VM. Miraculously, the old IP was still whitelisted at KBank. Confirmed: The system wasn’t blocked by the bank; the issue was internal.
Investigation Steps
- Tested connectivity from dev machine to KBank API: blocked.
- Tested from inside the VM: not blocked—IP still whitelisted.
- Confirmed: No external firewall or IP issues.
- Problem isolated to something internal: code, SSL, or infra.
- Narrowed investigation to SSL and system health.
Debugging and the Real Culprit
Day 13
Syntax, Silence, and SSL
After hours of digging, realized the syntax errors in return functions stopped any logs or responses from being recorded. Once fixed, a new error surfaced: the SSL certificate was expired. The payment gateway couldn't connect, and nothing in the logs gave a clue until the code itself was fixed first.
Investigation Steps
- Fixed syntax errors in core return/response functions.
- Restored logging so errors would show up.
- Discovered SSL certificate was expired.
- No alerting or monitoring for certificate expiry.
- Root cause: SSL plus bad code hygiene.
- System finally revealed its real issue.
The Certificate Odyssey
Day 14
No One Knew Who Owned SSL
Contacted every possible person—no one knew where the last SSL cert came from, or who had access. Had to generate a new CSR, coordinate with the bank and a new provider, and rebuild the trust chain from scratch. Eventually, the system came back to life.
Investigation Steps
- Tracked down SSL certificate provider (after much chaos).
- Discovered no one submitted a CSR before.
- Generated a new CSR and requested a new certificate.
- Installed and configured SSL on the system.
- Finally restored payment gateway connectivity.
- Set up monitoring for SSL expiry going forward.
System Rebooted, Lessons Burned In
Day 15+
Alive, But Wiser
After two weeks of chaos, the business finally came back online. QR code payment, web, and app worked again. Monitoring and documentation processes were created—painfully late, but a lesson never forgotten.
Investigation Steps
- Created a new SSL certificate and installed it.
- Restored service: website, app, and payment gateway.
- Implemented monitoring for critical infra points.
- Started documenting tech stack and system layout.
- Promised never to run blind again.
- Business survived, but just barely.
Hard Lessons from the Edge
This story is a reminder: It takes just one point of failure—and a lack of documentation—to cripple a business. Always keep your knowledge, credentials, and infra visible, not just in people's heads. Disaster doesn't book an appointment.
The SSL Certificate Mystery
The SSL Certificate Mystery
Solving the Payment Gateway that stopped responding without any clues
Silent System
After VM came back online
Requests Coming In, But No Response
After bringing the VM back online, we found Docker and Nginx running. When testing requests from web to API and checking Nginx logs. Found that request data was reaching the system, but no response was being sent back. Suspected either system damage or KBank policy changes.
Investigation Steps
- Found Docker and Nginx running in VM
- Tested firing requests from web to API
- Checked Nginx logs - found requests were reaching
- No response being sent back at all
- No information on how old dev team contacted KBank
- No KBank API documentation available
Docker's Deep Mystery
Container Investigation
Only Syntax Errors Found
Went into Docker container and found syntax error logs, but no errors related to our system. Didn't understand why data from Nginx wasn't reaching Docker, since logs only showed syntax errors.
Investigation Steps
- Investigated inside Docker container
- Found syntax error logs in Docker
- No error messages related to our system
- Couldn't understand why Nginx data wasn't reaching Docker
- Logs only showed syntax errors
- Needed to find the error point
Reverse Engineering Hunt
Code and Endpoint Tracing
Hunting for KBank Endpoint in Code
Had to reverse engineer code in VM to find errors and identify KBank endpoints. No information remained - had to decode the system line by line to understand it.
Investigation Steps
- Reverse engineered all code in VM
- Searched for hidden errors in the system
- Hunted for KBank API endpoints in code
- Analyzed system structure from remaining code
- No documentation or manuals to help
- Had to guess system behavior from code alone
IP Whitelist Testing
KBank Connection Testing
Discovering IP Block Truth
Used dev machine to fire requests to KBank API and found IP blocking for non-whitelisted addresses. But when testing VM requests to KBank, found our VM wasn't blocked, meaning our IP could still connect.
Investigation Steps
- Used dev machine to test requests to KBank API
- Found KBank blocks IPs not on whitelist
- Tested VM firing requests to KBank API
- Found VM wasn't blocked by KBank
- VM IP could still connect successfully
- Concluded problem was from our system, not IP blocking
Debugging Syntax Errors
Code Fixing
Truth Hidden Behind Syntax Errors
Started debugging code and fixing syntax errors. Found Docker wasn't showing KBank logs because function written to return response had syntax error. After fixing syntax errors, discovered SSL Certificate had expired.
Investigation Steps
- Started debugging and fixing syntax errors in code
- Found return response function had syntax error
- Syntax error prevented logs from KBank appearing
- After fixing syntax errors, found expired SSL Certificate
- No logs because response function wasn't working
- Real problem was SSL Certificate expiration
SSL Certificate Mystery
SSL Provider Investigation
SSL from Unknown Origin
Contacted team to find SSL service provider information. Received latest SSL submission data and found it was SSL issued by unknown source. Contacted provider and found no CSR data was sent to SSL provider.
Investigation Steps
- Contacted team for SSL provider information
- Received latest SSL submission data
- Found SSL was issued by unknown source
- Contacted provider about CSR origin
- Found no CSR was sent to SSL provider
- Created new CSR and requested SSL Certificate
System Back Online
Problem Solved
Payment Gateway Working Again
After creating CSR and requesting new SSL certificate, system returned to normal operation. Customers can use QR Code Payment normally and future prevention systems were established.
Investigation Steps
- Created new CSR (Certificate Signing Request)
- Requested new SSL Certificate from provider
- Installed new SSL Certificate into system
- Payment Gateway returned to normal operation
- Customers can use QR Code Payment again
- Created SSL expiration monitoring system
Lessons from SSL Certificate Mystery
This case taught us that syntax errors can hide real problems, and lack of SSL certificate monitoring can cause issues without notice. Having good alert systems and documentation is critically important.
Ready to Transform Your
Technology Strategy?
Let's discuss how we can drive innovation and growth across your organization. Whether it's strategic consulting, technology leadership, or speaking engagements.